EasyStealer is a dangerous Trojan malware infection created by cyber criminals with the motive of making money online through illegal and fraudulent methods. This dubious infection is a sneaky piece of threat that is able to attack all versions of Windows PC. However, older versions like XP/Vista and Windows 7 are more vulnerable to this infection. Read this guide to know how to get rid of this infection easily from your computer.

Threats like EasyStealer keep getting back on the PC if all associated files are not removed. So you are advised to use a powerful Malware Removal Tool to run a thorough scan of your PC and delete all threats at once.
Compatible with: Windows 11/10/8/7 (32 Bit and 64 Bit)
What is EasyStealer
EasyStealer is a kind of computer menace that secretly intrudes on the targeted machine and enjoys controlling the compromised system remotely. It is a violent Trojan malware that is ready to intrude on any Windows computer and keep hidden for an extended time while not being detected. It can change its name to disguise its presence on your PC which is why most security programs fail to detect it soon enough before it causes any severe problem.
Users don’t usually find out about EasyStealer virus until it starts doing its evil work. It is very important that if you suspect the presence of this infection on your machine, you must check your system thoroughly and remove it properly to avoid any serious altercations in the future.

Threats like EasyStealer virus can be very dangerous not only to the infected system but to the user as well. In today’s modern era, everybody likes to store their private and sensitive information on their PC for safekeeping and simple access. If anyhow your computer gets hacked or attacked by a nasty Trojan malware that can destroy your important files and transmit your personal information to hackers.
EasyStealer virus is programmed to collect personal details of the user like social media login passwords, credit card numbers, IP addresses, etc. by tracking browsing history and recording keystrokes. It is a very significant threat because it carries out a very sophisticated attack on the victimized machine from multiple sides. This nasty virus will start a series of malicious activities that will completely destroy your computing experience. The working of each explicit Trojan virus is completely different and fully depends on why it was created, however, they all have some quite common qualities.
Issues caused by a typical Trojan virus
- Sneak into the targeted computer without users’ permission.
- Redirect your browser to malicious sites and show annoying pop-ups.
- Steal your passwords and use a keylogger to record your keystrokes.
- Collect your personal and sensitive information and share it with hackers.
- Disable your antivirus in addition to the firewall to make the system more vulnerable.
- It can Install other threats and malware on your system secretly.
- Show fake tech support pop-ups that can lure you into a scam.
- It can allow hackers to remotely access your system without permission.
EasyStealer: Threat Analysis
| Name | EasyStealer |
| Type | Trojan |
| Threat Level | High (source to distribute other harmful threats). |
| Symptoms | Slow PC, unresponsive programs, unexpected errors, fake pop-ups, browser redirection. |
| Distribution | It could be distributed through spam emails, bundled freeware, porn, or torrent sites. |
| Damage | Steal personal data, corrupt files, bring other threats and give remote access to hackers. |
| Removal | Download SpyHunter 5 Anti-Malware |
How it infects your PC?
EasyStealer virus can get into your system through various different tricks. Hackers use lots of different methods to hook up new victims. Your PC can get this malware as an attachment to spam emails, sent by hackers with fake names. These emails may look genuine such as credit card bills, phone bills, bank statements, and so on. Most of the users fall for this and don’t check the sender’s email address or other information. Opening such emails, downloading attachments, and opening them without scanning can infect your PC.
This noxious Trojan malware is also being spread bundled with free third-party programs, shareware, cracked software, illegal patches, and fake updates. Apart from this, EasyStealer virus can also infect your machine when you visit malicious websites, porn, or torrent sites, click on misleading ads, or share files on unsafe websites. You can see this virus can easily sneak into your machine using any of these tricks and you won’t even notice until it starts creating problems.
How to Remove EasyStealer
Removing this dubious Trojan virus manually will take lots of time and even a little mistake can break your PC instantly. Regular Anti-virus applications fail to completely delete this infection, so we advise using SpyHunter 5 Anti-Malware.
It is a powerful Anti-Malware capable of removing threats like Trojans, Malware, Ransomware, Spyware, Browser Hijacker, Adware, Redirect Viruses, PUPs, Worms, Rootkits, etc. SpyHunter’s Advanced System guard will also block threats from intruding on your computer in the future.
How SpyHunter 5 Anti-Malware Works
- You will begin by downloading the software on your system for which you have to click on the below download button.
Geek’s Recommendation
Threats like EasyStealer keeps getting back on the machine if all associated files are not removed. So you are advised to use a powerful Malware Removal Tool to run a thorough scan of your PC and delete all threats at once.
SpyHunter 5 Anti-Malware offers a 7-day fully-functional Free Trial. Credit card required, NO charge upfront. No charge if you cancel up to two business days before the trial period ends. Read SpyHunter 5 Review and Free SpyHunter Remover details.
- Once the software has been downloaded, double-click on SpyHunter-Installer.exe to install the Anti-Malware program on your PC and proceed with the setup.
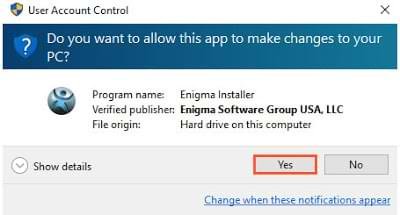
- After installation, you will need to launch the Anti-Malware application. From the welcome screen click on the Start Scan Now button to initiate a new scan of your PC.
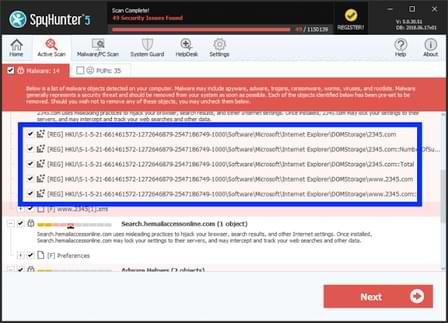
- Once the scanning process begins, it will take some time to run a thorough diagnostic of your PC and find all hidden threats and malware.
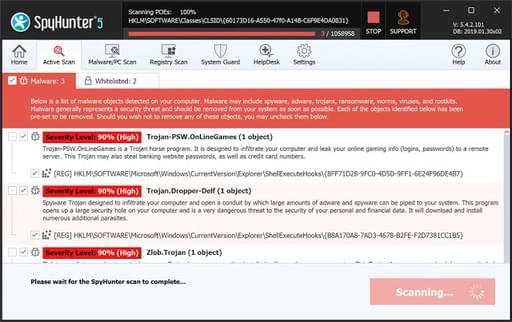
- Soon you will find a complete list of all the threats on your system screen. Then you will need to click on the Next button to delete all the viruses.

Leave a Comment