If all your files got .Datalock extension at the end then it means your computer is infected by a Ransomware Virus. This nasty .Datalock virus is created by hackers to encrypt victims’ personal files and force them to pay ransom money. This guide is aimed to help your remove this virus and restore your files without paying money to hackers.

Threats like Datalock keeps getting back on PC if all associated files are not removed. So you are advised to use a powerful Malware Removal Tool to run a thorough scan of your PC and delete all threats at once.
Special Offer SpyHunter 5 Anti-Malware offers a 7-day fully-functional Free Trial. Credit card required, NO charge upfront. No charge if you cancel up to two business days before the trial period ends. Read SpyHunter 5 Review, and Free SpyHunter Remover details.What is .Datalock File Virus
Datalock Ransomware is a harmful file encryption virus which is been reported by researchers to use a strong AES-256 encryption key algorithm to encrypt the files of an infected computer system. Like the other ransomware, .Datalock Virus also overtakes your confidential data and asks to pay a ransom from the victim. It generally takes the advantage of Windows’ default behavior of hiding the extension from file names to disguise the real extension of the malicious file hidden in it.

Once installed, .Datalock File Virus will completely take over your machine. It will encrypt all your personal and important files and add its own extension to the end of all your file names to mark them as encoded using its encryption key. It will demand ransom money to give you the decryption key that may decipher your data and you will be able to access your files. This .Datalock Virus Ransomware is a dangerous PC infection that leaves no choice to the user other than paying extortion fees but it is only aimed to cheat innocent users and thug their money, it will not decrypt your files as it promises.
Ransomware spread through various ways
.Datalock File Virus mostly intrudes on your computer bundled with free third-party programs that users download from shady websites. Those free applications may carry hidden attachments that can secretly get installed without asking permission. Spam email campaigns are another very often used method of malware spreading. Hackers hide malicious codes in attachments and send them to a large number of potential victims through automated software. When someone opens such an email and download attachments, threats like Datalock virus can easily get installed.
Unwanted pop-up ads and forced browser redirects are not only annoying but they can be used for malware distribution too. Cybercriminals use Redirect virus or adware like an infection to drive traffic on malicious sites which can trigger the download of .Datalock Virus and similar threats automatically. Browsing torrent websites and downloading pirated software could also bring nasty viruses to your computer. So you are advised to steer clear from these activities and scan your PC regularly for potential threats.
Datalock Ransomware: Threat Analysis
| Name | Datalock |
| Type | Ransomware, File-Encrypting virus |
| Extension | .Datalock |
| Threat Level | High (Encrypt all your data and Restrict access to your files). |
| Symptoms | Victims cannot access any files on their PC and find Ransom notes asking for money. |
| Damage | Datalock will encrypt your data by adding its extension to file names and demand ransom money for the decryption key |
| Distribution | It is mainly distributed through spam emails, bundled freeware, porn, or torrent sites. |
| Removal | Download SpyHunter 5 Anti-Malware |
| File Recovery | Download Data Recovery Software Now |
Ransom Message is left by Virus
As soon as the files get encrypted, Datalock Virus will leave a ransom note in every folder on your system to demand ransom money. It may also show a warning message on your computer screen when you try to access encrypted files. The ransom note that it has already placed on your system, contains brief information about encryption, how to recover your files, how much to pay, hackers’ contact details, and the payment method.
Sometimes you may get the dreaded screen from Datalock Ransomware demanding the ransom for which you must not proceed further or take any action in hurry. Paying the ransom money does not guarantee the decryption of your files safely. Most of the ransomware victims who choose to pay the ransom amount to get the decryption key, end up losing both their files and money.
The Ransom note left by this virus contains the following instructions :YOUR PERSONAL ID:
-
/!\ YOUR COMPANY NETWORK HAS BEEN PENETRATED /!\
All your important files have been encrypted!
Your files are safe! Only modified. (RSA+AES)
ANY ATTEMPT TO RESTORE YOUR FILES WITH THIRD-PARTY SOFTWARE
WILL PERMANENTLY CORRUPT IT.
DO NOT MODIFY ENCRYPTED FILES.
DO NOT RENAME ENCRYPTED FILES.
No software available on internet can help you. We are the only ones able to
solve your problem.
We gathered highly confidential/personal data. These data are currently stored on
a private server. This server will be immediately destroyed after your payment.
If you decide to not pay, we will release your data to public or re-seller.
So you can expect your data to be publicly available in the near future..
We only seek money and our goal is not to damage your reputation or prevent
your business from running.
You will can send us 2-3 non-important files and we will decrypt it for free
to prove we are able to give your files back.
Contact us for price and get decryption software.
hxxp://gvlay6u4g53rxdi5.onion/21-R1Wu50TdwfSawiYyul068n 4111M5AVEW-7XTbtJyI2PI9MRCZpQLW5vQRakSWLkRt
* Note that this server is available via Tor browser only
Follow the instructions to open the link:
1. Type the addres "hxxps://www.torproject.org" in your Internet browser. It opens the Tor site.
2. Press "Download Tor", then press "Download Tor Browser Bundle", install and run it.
3. Now you have Tor browser. In the Tor Browser open "{{URL}}".
4. Start a chat and follow the further instructions.
If you can not use the above link, use the email:
diniaminius@winrof.com
soterissylla@wyseil.com
* To contact us, create a new mail on the site: protonmail.com
Make contact as soon as possible. Your private key (decryption key) is only stored temporarily.
IF YOU DON'T CONTACT US WITHIN 72 HOURS, PRICE WILL BE HIGHER.
Few points which show Ransomware infection :
- All your files will be encrypted and you cannot access them.
- Your files will contain strange and unknown extensions at the end.
- A text or HTML file of instructions can be found in every folder.
- Victims will be asked to pay the ransom in Bitcoins for the decryption key.
- All media files like audio, videos, images, and documents, database, etc. will be locked.
What to do after encryption
As said above, .Datalock File Virus encrypts the discovered files with a very strong cipher and makes them inaccessible. If your computer is infected by this virus, then it will keep encrypting your files until its removed. This virus can be very hard to remove as it makes various changes to the compromised system and create lots of files. You must remove all the associated files completely to get rid of Datalock Virus at once. We have created a guide that can help you delete this infection. Once done with the removal process, you can also try Data Recovery Software to see if it can restore your encrypted files in their original format.
Automatic Datalock Removal Guide
As you already know that, Datalock Virus is a notorious and cunning malware that is not hard to remove easily by any user through manual means. This virus can keep coming back on the infected computer through files and shortcuts or settings that it has already created on your machine. Removing all those at once is the only way to get rid of this infection and stop it from getting on your system ever again.
So the best way to remove Datalock effectively is to use a powerful Automatic Removal Tool and save your time and efforts. This software is a well-trusted and very powerful anti-malware program that can detect all hidden threats like Trojan, Ransomware, Worms, Spyware, Rootkits, and many others. It also provides 24X7 customer support and one-on-one Spyware HelpDesk support for Custom Malware removal. Advanced System Guard feature detects and removes threats in real-time. It has a very User-Friendly Interface and regular Malware updates make it most effective against the latest malware attacks.
How SpyHunter 5 Anti-Malware Works
- First, you need to click on the below download button to get the software.
Geek’s Recommendation
Some time threats like Datalock keeps getting back on the machine if all associated files are not removed. So you are advised to use a powerful Malware Removal Tool to run a thorough scan of your PC and delete all threats at once.Compatible with: Windows 11/10/8/7 (32 Bit and 64 Bit)
- Then double-click on the installer you downloaded to install the program.
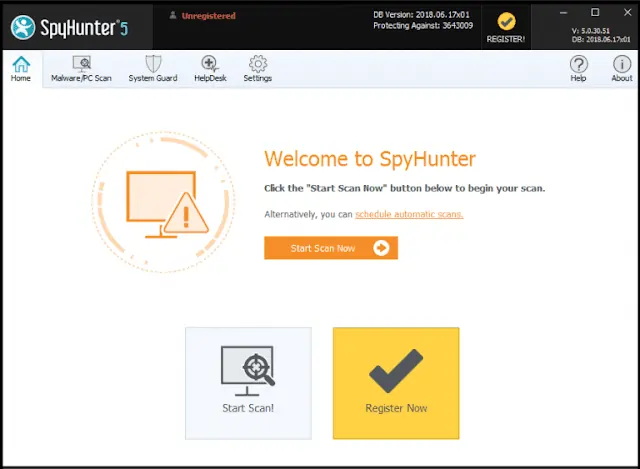
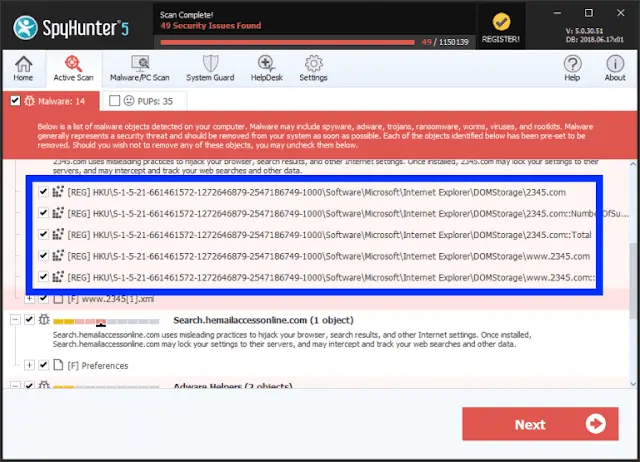
- Launch Anti-Malware application and Start Scan Now of your PC.
- The software will scan your PC for all hidden threats and viruses on your system.
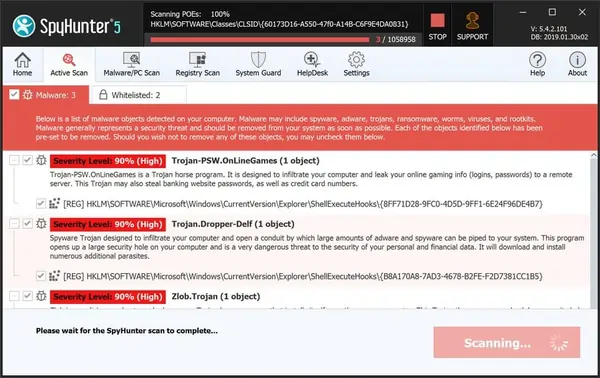
- Click on the Next button to see results and delete Datalock and other threats.
How To Recover Your Encrypted Files
Now all your files got encrypted by the .Datalock Virus then you need to recover your data without paying ransom money to hackers. If your files are important then you must have created a backup and you can use that backup to recover your files. If you don’t have a backup or this virus has encrypted your backup files, then you are left to seek professional help.
We recommend you use powerful data recovery software to restore your files encrypted .Datalock File Virus. It is a risk-free and smart way. You can just download the free version and scan your PC for files. There is a high probability that it can recover most of your files in a fraction of the amount that hackers are demanding. It is also needless to say that paying hackers will only motivate hackers to carry out more attacks.
- First, you need to download Data Recovery software on your PC.
Download Data Recovery Software Now
- Install the program, launch it then select the Data type to recover, and click the Next button.
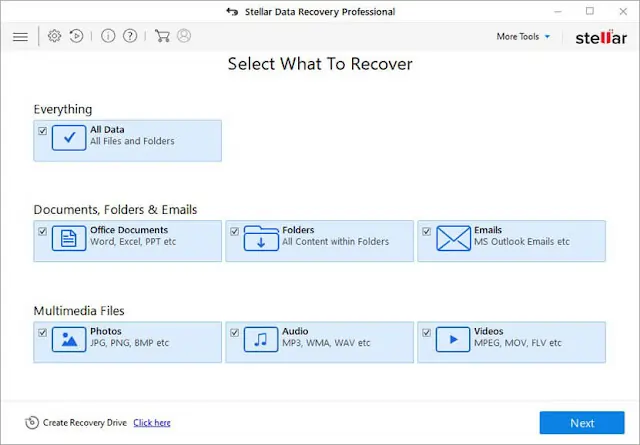
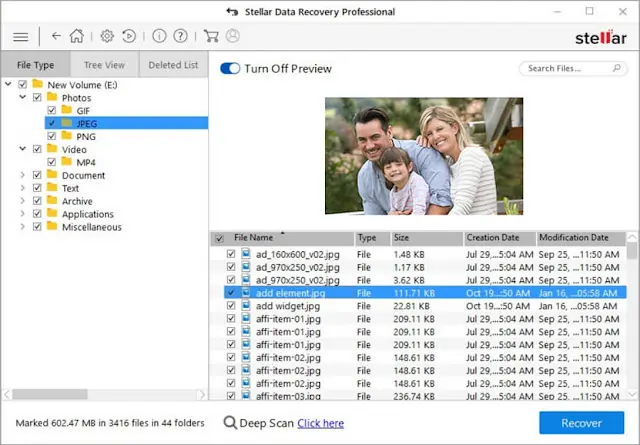
- Select the location from where you want to recover data and click the Scan button.

- After the scan, software will list all files, select them and click the Recover button.
Manual Datalock Removal Guide
- You have done this before, which means you have experience in removing the virus manually;
- That you know your way around PC and all necessary process and applications;
- You know about Registry entry and the Serious repercussions of any mistake;
- Make sure you can reverse any mistake made during .Datalock Virus manual removal.
If you don’t attain any of the above standards, then manual removal could be a very risky idea. It is most likely best for you to use the Automatic Malware Removal Tool to find and delete Datalock Virus, which is totally secure and efficient method.
Compatible with: Windows 11/10/8/7 (32 Bit and 64 Bit)
Start PC in safe mode with networking
- Press Windows Key + R buttons together on the keyboard.
- Type msconfig in the Run Box then click the OK button.
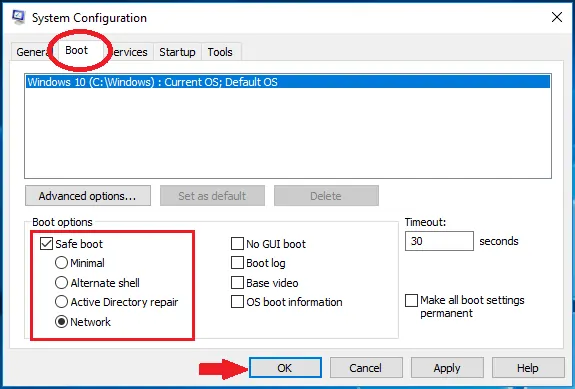
- Click on the Boot tab then the System configuration window will appear.
- Choose Safe Boot, check the network box, Click Apply, and press the OK button.
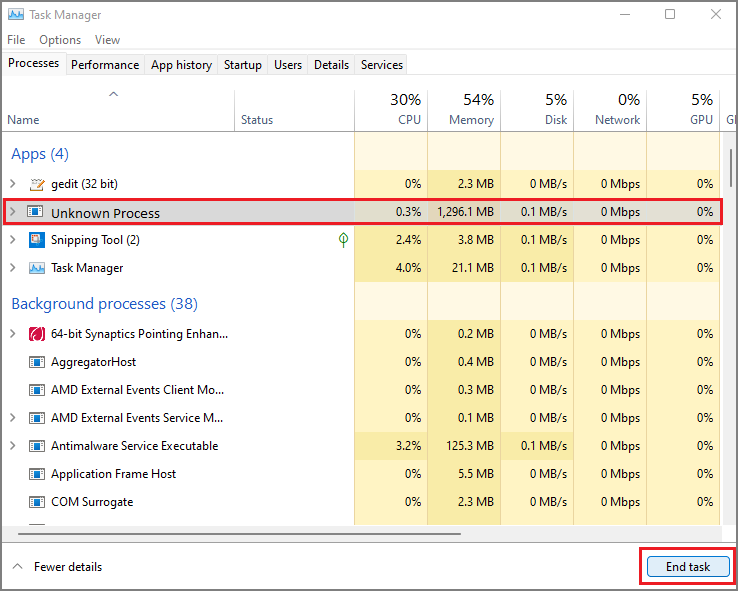
Kill Malicious Process From Task Manager
- Press Windows Key + R buttons together on the keyboard.
- Type taskmgr in Run Box and then click the OK button.
- Find Datalock related or any malicious process.
- Now right-click on it then click End process.
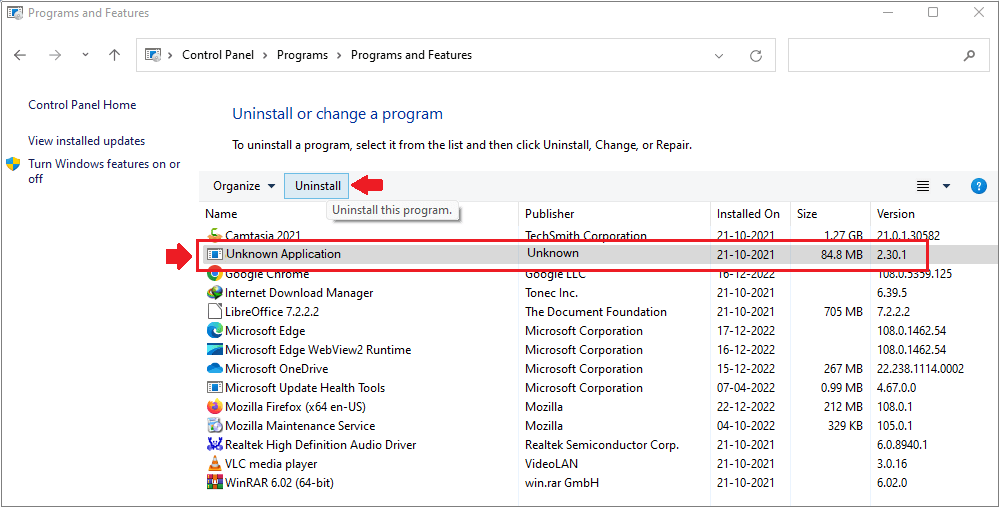
How To Uninstall Datalock from Windows PC
- First of all Press Windows Key + R buttons together.
- Type appwiz.cpl in the Run box and then click the OK button.
- Now Programs and Features windows will appear on the screen.
- Find and remove all Datalock related or malicious programs.
Compatible with: Windows 11/10/8/7 (32 Bit and 64 Bit)
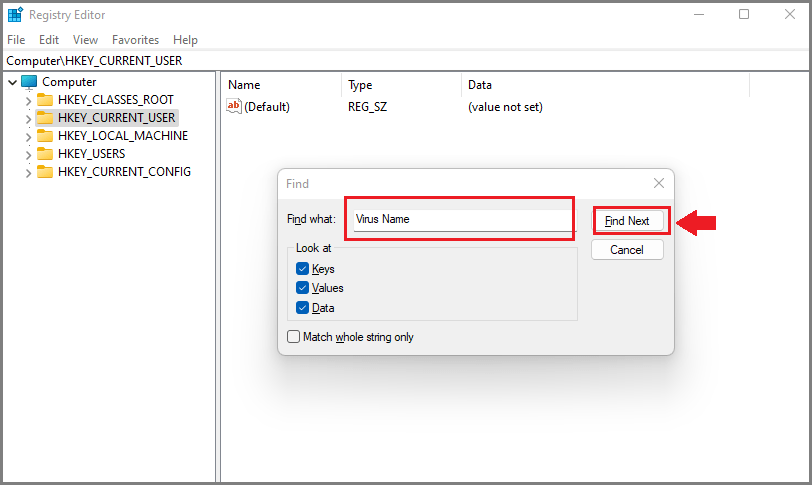
Remove Virus related Windows Registry entries
- Press Windows Key + R buttons together on the keyboard.
- Type taskmgr in Run Box and then click the OK button.
- Registry Editor will open, then press CTRL +F buttons together.
- Now type Datalock and then click on Find Next button.
- Find all the related entries and delete them one by one
Delete Virus related files from your PC
When a threat gets on to a PC, it most likely creates some files at different locations on the system. These files are used to perform a specific action and also help malware in getting back to the computer once it’s removed. So you just need to find also delete all those files associated with this .Datalock File Virus. For that follow the below instruction :- Press Windows Key + R buttons together on the keyboard
- Type each of the following in Run Box and press the OK button
- %AppData%
- %LocalAppData%
- %ProgramData%
- %WinDir%
- %Temp%
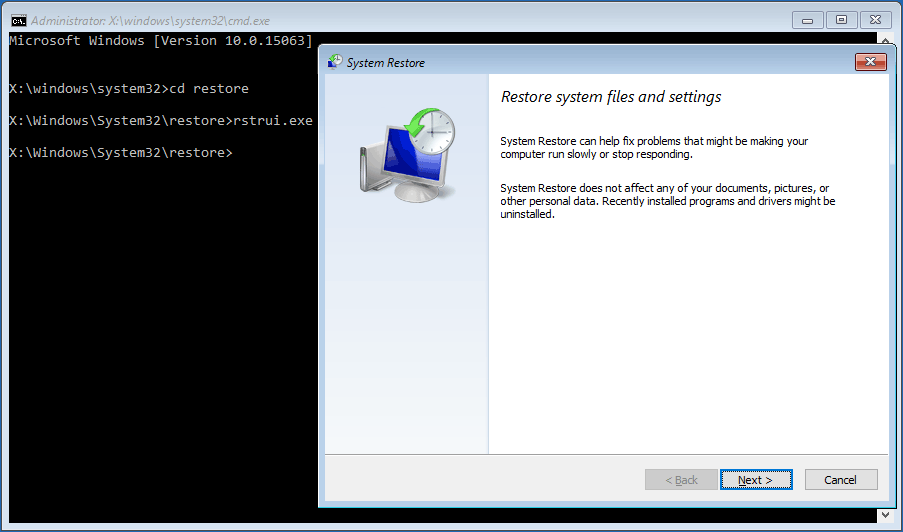
Remove Datalock Virus via system restore
- Press Windows Key + R buttons together on the keyboard.
- Type cmd in Run Box and then click the OK button.
- Type cd restore and press Enter, then type rstrui.exe and press Enter.
- When the System Restore window opens on your computer screen click the Next button, then choose a System Restore point you have created in the past and click the Next button.
- Finally, click on the Yes button to start the system restoration process.
Note: This will only work if you have a restore point set on your PC or it will give an error message. Restoring the computer to a previous version may or may not remove .Datalock File Virus. Most of the time, viruses just delete all the restore points. If this trick does not work for you then don’t get disappointed.
After restoring your computer, we recommend you run a thorough scan of the PC using a Powerful Anti-Malware program to detect and remove any hidden threats. In most cases, viruses may spread through any files outside of the C drive because system restoring only affect the C drive. There may be some Virus related files hiding your PC, and it never hurts to double-check.
Sometimes, system restore doesn’t work or viruses can just remove the restore points. As such you will probably have no other choice than to choose the Automatic Removal Process. It is the best and error-free method to find and remove threats from your computer. Additionally, you should also check some important malware prevention tips provided here in this guide to avoid similar virus attacks in the future.
Remove Datalock From MacOS
If you are a mac user, and your machine got infected by this nasty file-encrypting malware then you need to remove it as soon as possible. Although Mac systems are quite safe they still do get infected. So you can delete this infection using the below steps:Stop Malicious Program From Activity Monitor
- First, you need to open Utilities folder on your Mac system.
- Find the Activity Monitor icon and double-click on it to open it.
- Find Datalock related process, click the cross button from the upper left side corner to end task.
- A pop-up dialogue box will appear on the screen, click on the Force Quit button.
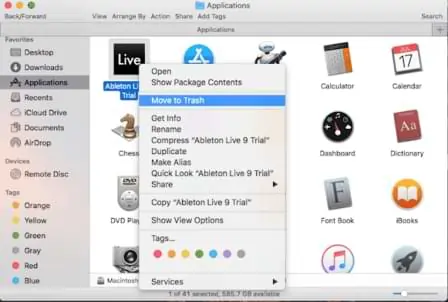
Remove Virus From Application Folder
- First, go to the Dock option (bottom of your screen) then click on Finder App.
- Now you have to open the Applications Folders to see all the programs.
- Find Datalock or any other unwanted program then move it to Trash.
Attention: If you are not tech-savvy, then it could be quite difficult to remove Datalock manually from your Mac. The best way is to download ComboCleaner Mac Anti-Malware and see if it can detect all hidden threats and viruses on your computer. It’s really super easy and you should give it a try.
ComboCleaner Mac Antivirus allows you to scan your Mac for threats and viruses for free, but you will need to purchase a full license to remove found threats. Read EULA.Tips To Prevent .Datalock Virus in Future
- Use a good anti-virus, be it a free version but don’t use cracked security programs.
- Make sure that your Windows firewall is active, so it can block upcoming threats.
- Keep your Windows/Mac OS and other programs updated to avoid vulnerabilities.
- Download updates only from official websites, don’t use suspicious sites.
- Never download and install pirated software, games, or illegal patches on your PC.
- Do not open spam emails from an unknown sender and scan all attachments before opening.
- Never download freeware third-party programs from unreliable sources or websites.
- Avoid connecting your PC to unsafe public Wi-Fi to protect your privacy.
- You can also use a VPN to spoof your connection and avoid malicious sites.
- Create a system restore point on your system for security purposes.
- Keep backup of all your important files to avoid data loss.
If you are also a Victim of Datalock virus then you should report this cybercrime incident to legal authorities in your county. Here is the list of some of the official government websites for reporting fraud and scam activities:
- United States – Guard Online
- Australia – SCAMwatch
- United Kingdom – Action Fraud
- New Zealand – Consumer Affairs Scams
- Canada – Canadian Anti-Fraud
- Ireland – An Garda Síochána
- India – National Cybercrime Reporting Portal
You can also search to find the Internet Crime Authority in your country. Meanwhile, it will not help you remove or restore your files in any way but it’s merely information to authorities. Once you register your complaint, authorities might look into and take preventive measures to stop further attacks. However, don’t get lured by third-party criminal reporting sites or fake technical support websites. They are more like to cheat you instead of helping you.
Some time threats like Datalock keeps getting back on the machine if all associated files are not removed. So you are advised to use a powerful Malware Removal Tool to run a thorough scan of your PC and delete all threats at once.
Compatible with: Windows 11/10/8/7 (32 Bit and 64 Bit)

Leave a Comment