Powd Ransomware or also known as .Powd File Virus is a notorious data locker virus. It is the latest variant of STOP/Djvu Ransomware that is circulating online through deceptive means. It restricts access to all your personal data (images, videos, documents, etc.) by encrypting them.
If all the files on your PC got “.powd” extension at the end and you cannot access them, it is a sign that your system is attacked by this ransomware. This malware is targeting innocent PC users and forcing them to pay huge ransom money by encrypting their files. If you are also a victim of this virus and want to learn how to remove Powd Virus and recover your files then read this guide.
Threats like Powd virus keep getting back on the PC if all associated files are not removed. So you are advised to use a powerful Malware Removal Tool to run a thorough scan of your PC and delete all threats at once.
Compatible with: Windows 11/10/8/7 (32 Bit and 64 Bit)
What is Powd Virus
Powd File Virus is a variant of STOP/Djvu Ransomware. Similar to its other variants, this notorious file-encrypting virus is an excellent intruder. It is capable to hit any version of Windows computer without users’ permission. It is created with the sole motive of blackmailing victims to pay the ransom by encrypting their personal files.
In today’s digital world, everyone’s computer is a gold mine of information that may not have any value to others but it has great value to the owner. Creators of this Powd Virus knows this fact that’s why they target the personal files and documents of the users to force them into paying hefty ransom money to get their precious data back.
.Powd File Virus is a file-encrypting malware with very deep roots in the online extortion business. It belongs to the infamous STOP (DJVU) Ransomware family which has successfully launched more than 330 ransomware variants. In the recent past, these file-encrypting threats have terrorized millions of users around the world. It directly means the creator of this Powd virus is extremely smart and ruthless.
Working of Powd File Virus
Makers of this Powd Virus keep releasing new variants of their file-encrypting malware after regular intervals to make an illegal profit by cheating innocent victims. This data-locker virus is able to infect all versions of Windows computers and encrypt all the important files stored on that PC.
You will find that it adds “.powd” extension to the end of all your file names, for example, the file “mypicture.jpg” will get changed to “mypicture.jpg.powd” and you will not be able to access such altered files. Actually, this extension is a marker that shows your files are locked, and then you will find the ransom note “_Readme.txt” on your computer left by this virus to demand ransom money.
This is the screenshot of the ransom message “_readme.txt” left by this virus on the infected PC:

If your system is infected by this Powd malware infection, then all your files, documents, videos, music, pictures everything would be locked. All your files will still be there on your computer as you have put them but you can access them. This threat uses a very powerful encryption algorithm to lock down your files.
It is impossible to break the encryption without a decryption key and unfortunately, there is no Powd ransomware decryption tool available. This deceptive Virus will also leave a ransom note on your computer to explain what happened to your files and how you can get them back.
Ransom demand is a trick
Creators of Powd Virus simply asks users that there is no other way to decrypt .Powd files other than buying the private decryption key generated for your computer. Keep one thing in mind the decryption key for every user is different and it is completely unique.
They have set an amount of $980 USD as the primary ransom fee but they are willing to give you a 50% discount. However, victims need to pay the money within 72 hours of infection. They are baiting the victims to fall for this discount offer and pay $490 USD without seeking help from anyone else. It is simply a scam trick to manipulate users into paying money without looking for other options.
The ransom note “_Readme.txt” contains the following text message:
ATTENTION! Don’t worry, you can return all your files! All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key. The only method of recovering files is to purchase decrypt tool and unique key for you. This software will decrypt all your encrypted files. What guarantees you have? You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information. You can get and look video overview decrypt tool: https://we.tl/t-gSEEREZ5tS Price of private key and decrypt software is $980. Discount 50% available if you contact us first 72 hours, that’s price for you is $490. Please note that you’ll never restore your data without payment. Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours. To get this software you need write on our e-mail: support@sysmail.ch Reserve e-mail address to contact us: supportsys@airmail.cc Your personal ID: -
How your Computer got infected
.Powd File Virus is a sneaky malware that could alter your system security in various different ways. Most of the time, scam email techniques are used to drop this malware directly into your Inbox with some legit name. When users open such kinds of emails, the virus silently slips into the machine and gets installed secretly.
Threats like this also normally spread through bundled freeware or shareware programs, cracked software, illegal patches, etc. that users normally download from the Internet for free and even stop their anti-virus protection to install those programs. If cybercrooks embed their codes in such types of files, then the rest is very easy.
Apart from this, Powd Virus Ransomware could also alter your system security when you browse porn websites, down torrent files, share files on unsafe networks, and click on misleading ads that redirect your browser to phishing websites. As you can see there are various different probabilities through which your system can get infected and you won’t even know.
Powd Ransomware: Threat Analysis
| Name | Powd |
| Type | Ransomware, File-Encrypting virus |
| Family | STOP/DJVU Ransomware |
| Extension | .Powd |
| Threat Level | High (Encrypt all your data and Restrict access to your files). |
| Symptoms | Victims cannot access any files on their PC and find Ransom notes asking for money. |
| Damage | Powd Ransomware will encrypt your data by adding “.Powd” extension to file names and demand ransom money for the decryption key |
| Ransom Note | _Readme.txt |
| Ransom Amount | $490 USD to $980 USD |
| Distribution | It is mainly distributed through spam emails, bundled freeware, porn, or torrent sites. |
| Removal | Download SpyHunter 5 Anti-Malware |
| File Recovery | Download Data Recovery Software |
Do Not Pay RANSOM Money
Paying ransom money to decrypt Powd virus infected files is a big mistake. Cybercriminals behind this threat only want your money. They stay anonymous by asking you to pay through cryptocurrency like BitCoin. Once you pay the ransom, you cannot track who got your money. So chances of fraud are very high. They will have no reason to give you the decryption key after getting paid.
If somehow you will get the decryption key, what is the guarantee that it will work? That decryption key may bring more viruses to your PC. It can steal your personal information or even completely remove all your files. So it is not a good idea to trust criminals. You should focus on removing Powd file virus from your computer. If you have a backup of your files then you might get lucky. Do not attempt file recovery without removing the virus or it will encrypt your backup files as well.
You can also try third-party data recovery software for your files but still, you have to first delete this infection. There is no way to recover your files until you remove Powd virus from your system. So you are advised to follow the given instructions carefully to get rid of this malware and restore your files without paying ransom money.
How To Remove Powd File Virus
Follow this guide carefully to remove this virus completely from your system. Below you can find step-by-step instructions on how to effectively get rid of this nasty threat easily. Removal of threats like Powd Virus is never easy, so we have simplified the process for you in several small steps.
Quick Summary of Removal Instructions:
- Automatic Powd Virus Removal Guide
- How To Decrypt .Powd Files
- Manual Powd Virus Removal Guide
- Start PC in Safe Mode With Networking
- Kill Malicious Process From Task Manager
- Remove Virus From Windows Registry Editor
- Remove Powd Virus via system restore
- Prevent Powd Virus in Future
Please Bookmark This Page by pressing the {ctrl+D} button or print it out on paper before you start the removal process because you may need to restart your PC or browser.
Automatic Powd Virus Removal Guide
It can be hectic to remove threats from an infected PC but the use of powerful Anti-Malware can make it quite easy. SpyHunter anti-malware can help you to remove Trojan, Ransomware, Spyware, Adware, PUPs, etc. easily. You can scan your system for Powd virus and all other hidden threats at once. All you need to do is to download this software and run a new scan on your PC.
It will find all the threats and viruses in no time and save you lots of time and effort. This amazing software also provides 24X7 customer support and one-on-one Spyware HelpDesk support for Custom Malware removal. Advanced System Guard feature detects and removes threats in real time. It has a very User-Friendly Interface and regular Malware definition updates make it most effective against the latest attacks.
How SpyHunter 5 Anti-Malware Works
- You will begin by downloading the software on your system for which you have to click on the below download button.
Geek’s Recommendation
Threats like Powd Virus keep getting back on the machine if all associated files are not removed. So you are advised to use a powerful Malware Removal Tool to run a thorough scan of your PC and delete all threats at once.
Compatible with: Windows 11/10/8/7 (32 Bit and 64 Bit)
- Once the software has been downloaded, double-click on SpyHunter-Installer.exe to install the Anti-Malware program on your PC and proceed with the setup.
- After installation, you will need to launch the Anti-Malware application. From the welcome screen click on the Start Scan Now button to initiate a new scan of your PC.
- Once the scanning process begins, it will take some time to run a thorough diagnostic of your PC and find all hidden threats and malware.
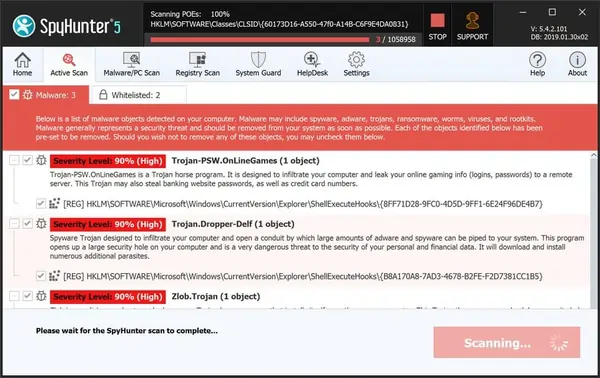
- Soon you will find a complete list of all the threats on your system screen. Then you will need to click on the Next button to delete all the viruses.
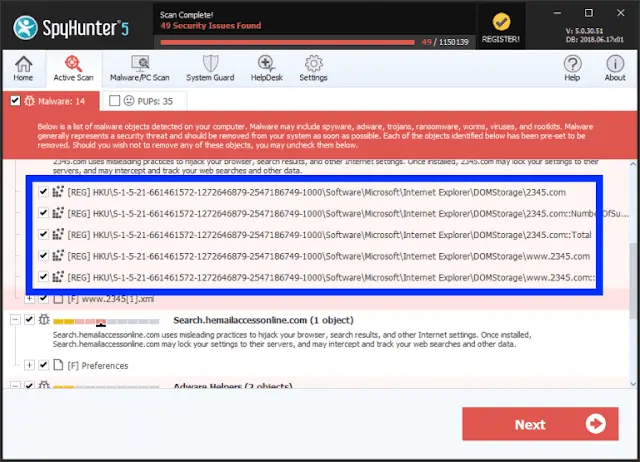
How To Decrypt .Powd Files
As there is no Powd ransomware decryptor available, you will need to use alternate options to restore your files. The first one is to use the backup. If you have created a backup of your important files then it is going to be quite easy. However, if you don’t have any backup files or they also got encrypted by the virus then you will have to try a data recovery software.
We recommend using Stellar Data Recovery software because it is a powerful and trusted data recovery software. Paying ransom money is not ideal because it will only motivate hackers to carry out more attacks. You can wait for any free decryptor to be launched but it can take forever. Download the free trial version of data recovery and scan your PC for files. It may be able to recover some of your files and save you lots of money.
- Click on the below download button to get started instantly with the data recovery process on your PC.
Download Data Recovery Software Now
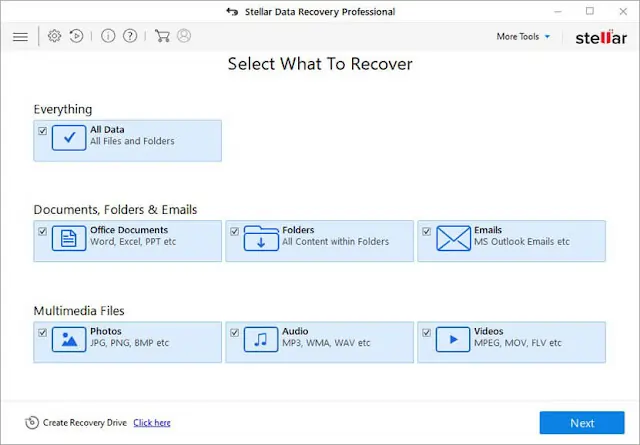
- After the download click on the installer file and complete the software installation. Then launch the application and select the Data type to recover, and click the Next button.
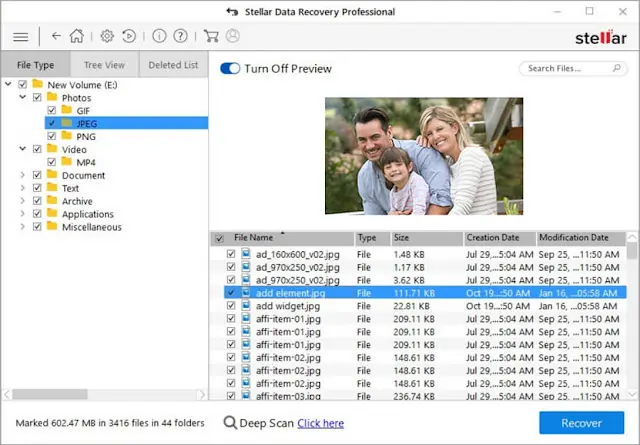
- After the selection of data, you will need to select the location from where you want to recover data. Choose the location and then click on the Scan button.

- The software will take some time to scan your system. You will see a list of all the files that can be recovered. You can preview them or click on the Recover button to save them.
Manual Powd Virus Removal Guide
Attention! For the safety of your system, please confirm a few things before you begin manual removal:
- You have done this before, which means you have experience in removing the virus manually;
- That you know your way around PC and all necessary processes and applications;
- You know about Registry entry and the Serious repercussions of any mistake;
- Make sure you can reverse any mistake made during virus removal.
If you don’t attain any of the above standards, then manual removal could be a very risky idea. It is most likely best for you to use the SpyHunter 5 Anti-Malware which is totally secure and efficient method.
Compatible with: Windows 11/10/8/7 (32 Bit and 64 Bit)
Start PC in safe mode with networking
- Click on the Windows and R keys together on your keyboard to open the Windows Run Box.
- Now you will need to type in MSConfig and then click the OK button.
- The System configuration settings box will appear on your computer screen.
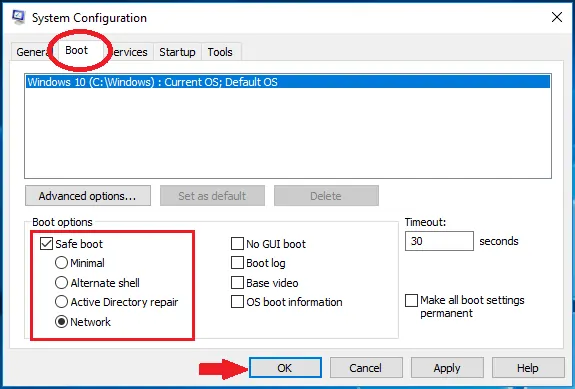
- Click on the Boot tab, check the Safe Boot option, and select the network box,
- Finally, you will have to click on Apply and then press the OK button.
Kill Malicious Process From Task Manager
- Open the Windows Rub box again on your PC by pressing the Windows and R keys together on your keyboard.
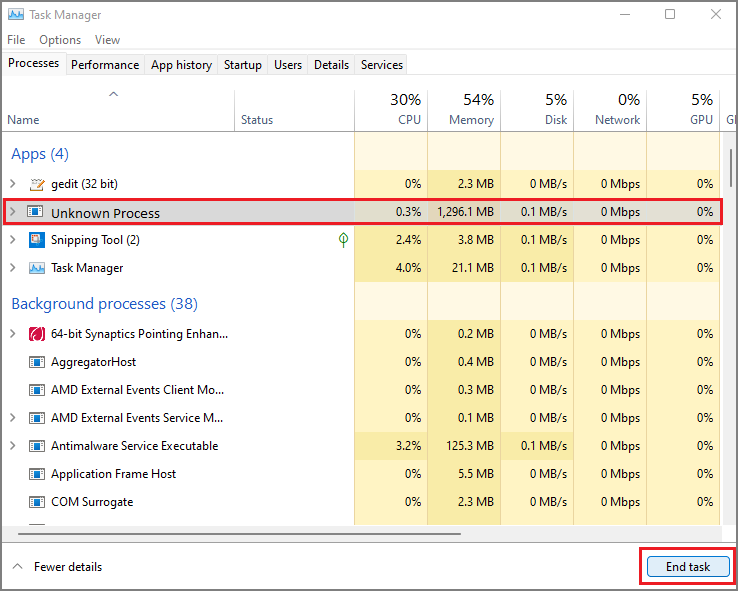
- This time you will have to type in taskmgr and then click the OK button to open Windows Task Manager. Look for any unknown or malicious running on your system.
- Select the process which is taking lots of systems resources and then click on the End Task button.
Uninstall Powd Virus from Control Panel
- Again you will need to open the Windows Run Box, so press the Windows and R keys together.
- This time you need to open the Windows Control Panel, so type in appwiz.cpl and then click the OK button.
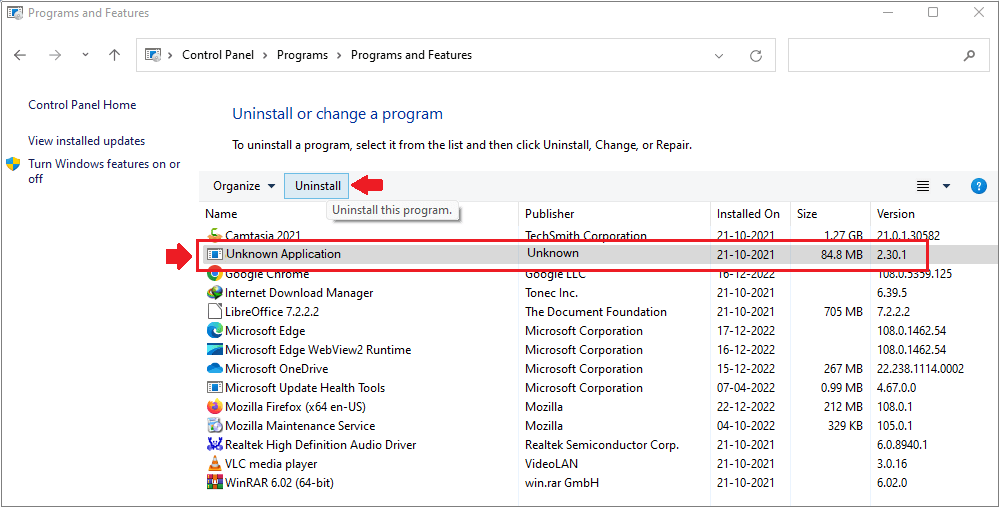
- Programs and Features windows will appear on your computer screen with a list of all the installed applications.
- Now you need to look for any unknown or virus related program and then Uninstall it from your PC.
Remove Powd Virus From Registry Editor
- Again open the Windows Run Box on your PC by using the Windows and R keys.
- To open the Windows Registry Editor, type in Regedit and click the OK button.
- Now you will have to find the virus related registry files and remove them.
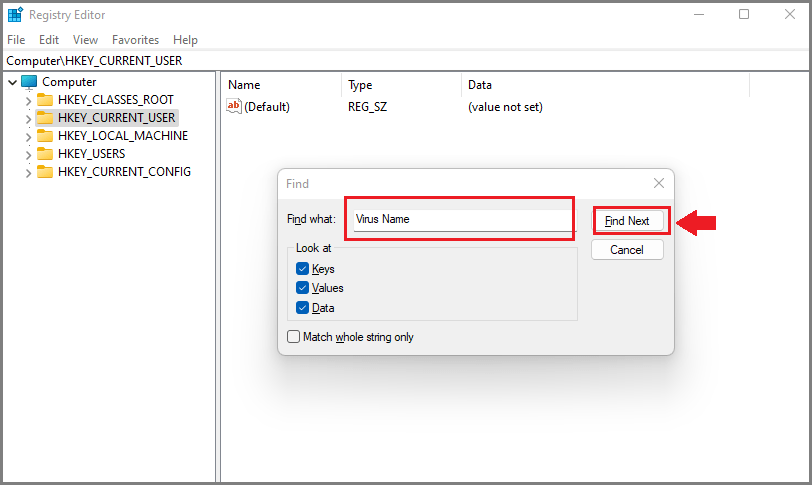
- Press CTRL and F keys together on the keyboard to start a Find query.
- Type the virus name and click on Find Next button to find malicious entries and delete them.
Warning: Meddling with Windows Registry files might not be a good idea if you don’t have advanced knowledge about registry files. Deleting the wrong file can break down your entire system. Proceed at your own risk, or just skip this step. You can choose the Automatic Removal method and avoid all the problems.
Compatible with: Windows 11/10/8/7 (32 Bit and 64 Bit)
Remove Malicious IP addresses from Windows Hosts Files
- To open the Windows hosts file, simply press the Windows and R keys together on the keyboard.
- Type C:\Windows\System32\drivers\etc in Run Box and then click the OK button.
- Now you will need to access the Windows hosts file using Notepad.
- Most threats add malicious IP addresses here to automatically connect to remote servers.
- Delete all the malicious IP addresses below the localhost and save the file.
Delete Virus related files from your PC
When malware infects your system, it normally creates several malicious files and spread them at different locations. After you remove the malware, these leftover files help them to get back to your computer. Remove all virus related files at once by following the below instruction :
- Open the Windows Run Box again by using the Windows and R keys together.
- Now you will open the below paths one by one using the Run Box and remove malicious files.
- %AppData%
- %LocalAppData%
- %ProgramData%
- %WinDir%
- %Temp%
For the first four options, look for any recent folder related to the Powd File Virus and remove them. For the Temp folder, you can delete all the files at once. Use Ctrl, Shift, and Delete keys together for permanent removal.
Remove Powd Virus via system restore
- You will again need the Windows Run Box, so press the Windows and R keys together.
- Open the Command Prompt by typing in cmd and then clicking the OK button.
- Type cd restore and press Enter, then type rstrui.exe and press Enter.
- The System Restore window will get opened instantly then click on the Next button.
- Choose a System Restore point you have created in the past and click the Next button.
- Finally, when you will hit the Yes button, the system restoration process with start immediately.
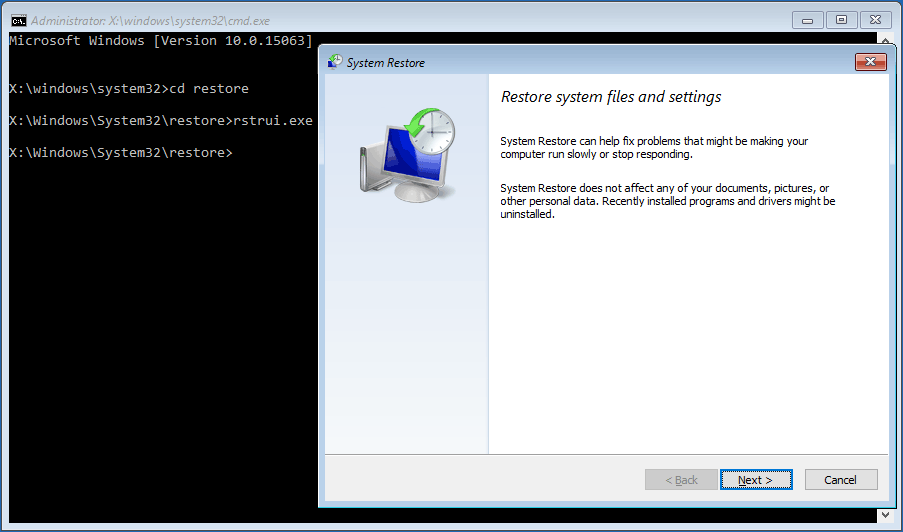
Note: System restore to remove a virus will only work if you have a restore point set on your PC. Otherwise, no changes will be made to your system and it will not remove any threats. Be advised, restoring the computer to a previous version does not always guarantee virus removal. Most viruses delete restore points, so don’t get disappointed if this trick does not work for you.
Prevent Powd Virus in Future
- Get a powerful Anti-Malware or Anti-virus to fight cyber threats. Free versions do not offer the best protection and cracked security programs can do more damage than good.
- Always keep your Windows firewall active, and your OS updated along with other important programs. Only download updates from official sites or reliable sources.
- Check HTTPS before entering your email, password, credit card details, etc. to any site. Do not visit sites that do not have SSL security. Also, don’t forget to Enable Phishing and Malware protection in Browser.
- Do not download or install any type of pirated software, games, or illegal patches. Avoid using shady sites to acquire freeware programs because they often use software bundling. Never install a program that asks you to inactivate your anti-virus software.
- Avoid opening spam emails from unknown senders. Always scan all the email attachments before opening them. Never click on any suspicious links with some too good to be true offers.
- Connecting your PC or mobile devices to unsafe public Wi-Fi is not a good idea. You can also avoid unwanted threats coming from malicious sites by using a VPN to spoof your connection.
- Keep regular backups of all your important data on external hard drives or cloud drives to avoid data loss in case of a ransomware attack. Also, create a system restore point on your system for security purposes.

Leave a Comment